2022 CryptoCTF
warm-up
Mic-Check
分值:19
考点:签到
Can you hear me?2022-Jul-Thu 12:20:26
If you can, enter your first flag:
1 | CCTF{Th3_B3sT_1S_Yet_t0_C0m3!!} |
easy
Klamkin
分值:61
考点:Congruence
challenge
We need to have a correct solution!
1 | nc 04.cr.yp.toc.tf 13777 |
1 | [root@VM-0-7-centos ~]# nc 04.cr.yp.toc.tf 13777 |
thought
exp
1 | from Crypto.Util.number import * |
result
1 | [+] Opening connection to 04.cr.yp.toc.tf on port 13777: Done |
Baphomet
分值:56
考点:已知明文攻击
challenge
1 | #!/usr/bin/env python3 |
thought
exp
1 | #!/usr/bin/env python3 |
result
1 | 48 |
medium-easy
SOTS
分值:49
考点:two_square
challenge
He who abides far away from his home, is ever longing for the day he shall return.
1 | nc 05.cr.yp.toc.tf 37331 |
1 | [root@VM-0-7-centos ~]# nc 05.cr.yp.toc.tf 37331 |
Thought
exp
https://www.alpertron.com.ar/QUAD.HTM
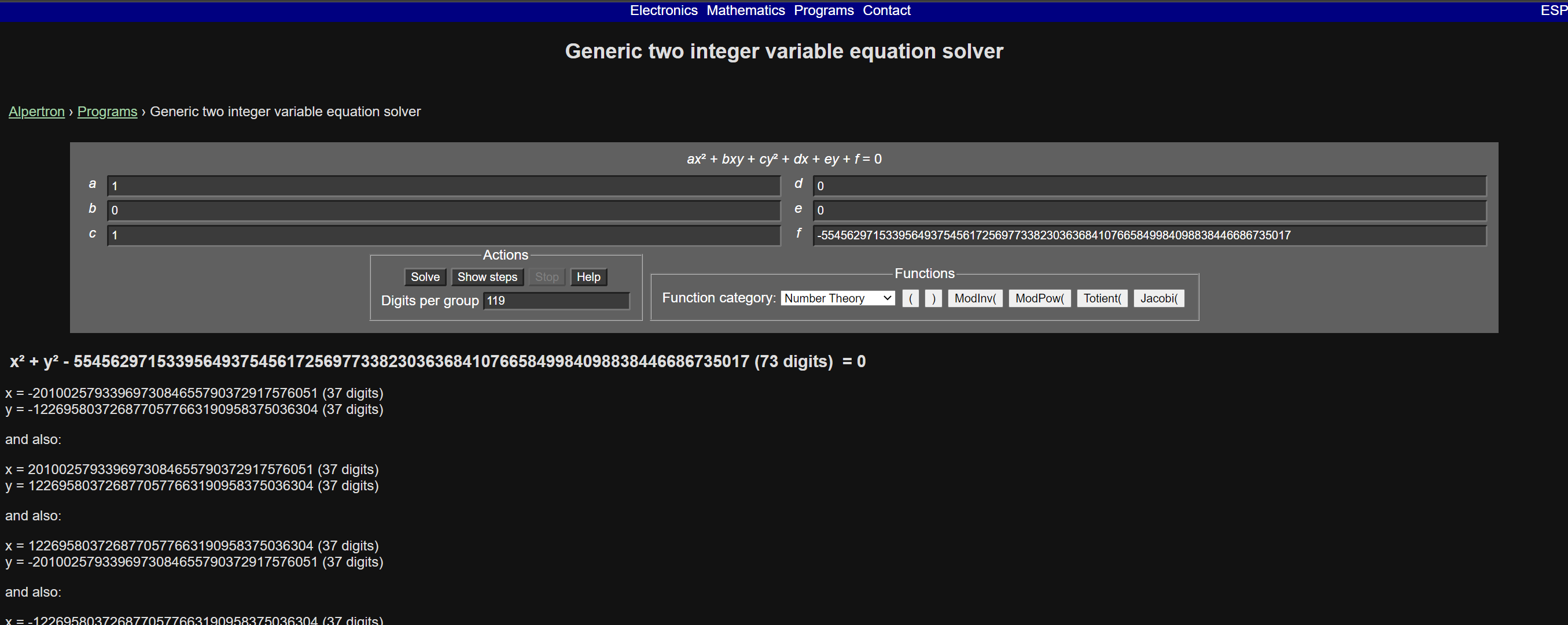
1 |
|
result
1 | root@VM-0-7-centos ~]# nc 05.cr.yp.toc.tf 37331 |
polyRSA
分值:42
考点:RSA
challenge
Hello RSA, my old friend!
1 | #!/usr/bin/env python3 |
Thought
exp
1 | n = 44538727182858207226040251762322467288176239968967952269350336889655421753182750730773886813281253762528207970314694060562016861614492626112150259048393048617529867598499261392152098087985858905944606287003243 |
result
1 | b'CCTF{F4C70r!N9_tRIcK5_aR3_fUN_iN_RSA?!!!}' |
Infinity castle
分值:131
考点:二次方、三次方、立方和、平方差、积分、泰勒展开
challenge
Can you break our new schema and decrypt the mixed encrypted message without having the public key and shared secret?!
1 | #!/usr/bin/env python3 |
Thought
diamond:$n^2$
triage:$n^3$
summarize:$\int_\infin \sqrt{n}=\frac{2}{3}n^{\frac{3}{2}}$
exp
1 | def xor(cip, key): |
result
1 | b'Never heard of using taylor series and integral beside RSA?!\nBut there are always ways to make things complicated\n\nCCTF{Mix1ng_c4lcUluS_w17h_Numb3r_The0Rry_S33ms_s7r0ng_cRyp70_Sch3m4!!}\n\nWe compute integrals with just measuring the area with a little fraction, forget about tough works!\nGood luck with the rest of CryptoCTF2022\x9a\x92W\xcf\xa2dl\x1a\x91\x96\'\x88\xec\xfez\xcd\xc2\xe7\x0bC\x90\xa3\xc7\xe7U\xb4F\xa535V\x19\x9b\x9e\xd4\xf7\xe7X\x02\x19Y\x86\xfa\x9f\x0b!\x9a\xc1\xd2\xcayG\x8af/\x14\xef\xf9\x1d\xc2\x9a\xcb\x9da}g8\xb8\\ 2~\xf3\xe3\xb6$\xb6i\x12\xd6\x82\xfac\x15\xeeVa[s\xa0S\x00y\x0c\x18\xc34\xbd\x96fd\xec\xcf\xb9\x02<Q\x8b\xb8\x9d\xd5\xefDu\xda\xd2\xf0\xc6g\x97\xf8\x952\x0c\rs=\x19.\x11"\x08\x81\xe7*\x87\xb8\xbd>\x82\n~\xf7l,\tu\x96}*\xab`\x17\xe7\xf4\xd7N^\xe3\xfe\xf3@\x1e\x1c\x15\xffC\xecVVr\xca\x8d\x03\xc5\xda\xd6\xbf=\xc6\x14+\xf2\x14N' |
Keydream
分值:105
考点:RSA
challenge
Everything is better homemade, we developed a homemade RSA, test it to see if it’s really better?
1 | #!/usr/bin/env python3 |
Thought
$f = phigh\cdot 2^x+unknow \cdot 2^y+plow$
exp
1 | n = 23087202318856030774680571525957068827041569782431397956837104908189620961469336659300387982516148407611623358654041246574100274275974799587138270853364165853708786079644741407579091918180874935364024818882648063256767259283714592098555858095373381673229188828791636142379379969143042636324982275996627729079 |
result
1 | 'Congratz, the flag is: CCTF{h0M3_m4dE_k3Y_Dr1vEn_CrYp7O_5ySTeM!}' |
Jeksign
分值:100
考点:丢番图方程
challenge
Solve the equation, we like to have the solution!
1 | nc 02.cr.yp.toc.tf 17113 |
1 | #!/usr/bin/env python3 |
Thought
$1337(z^4-x2)=31337(y^2-z^4)$
$(1337+31337)z^4=1337x^2+31337y^2$
$x=y=z^2$
exp
1 | from Crypto.Util.number import * |
result
1 | | Congrats, you got the flag: CCTF{4_diOpH4nT1nE_3Qua7i0n__8Y__Jekuthiel_Ginsbur!!} |
Volgo
分值:
考点:
challenge
There is no land behind the Volga!! The Soviets surround us,and we have only a single key table to communicate to the outside!! Hopefully, the Soviets wouldn’t be able read our messages.
1 | http://03.cr.yp.toc.tf:11117/ |
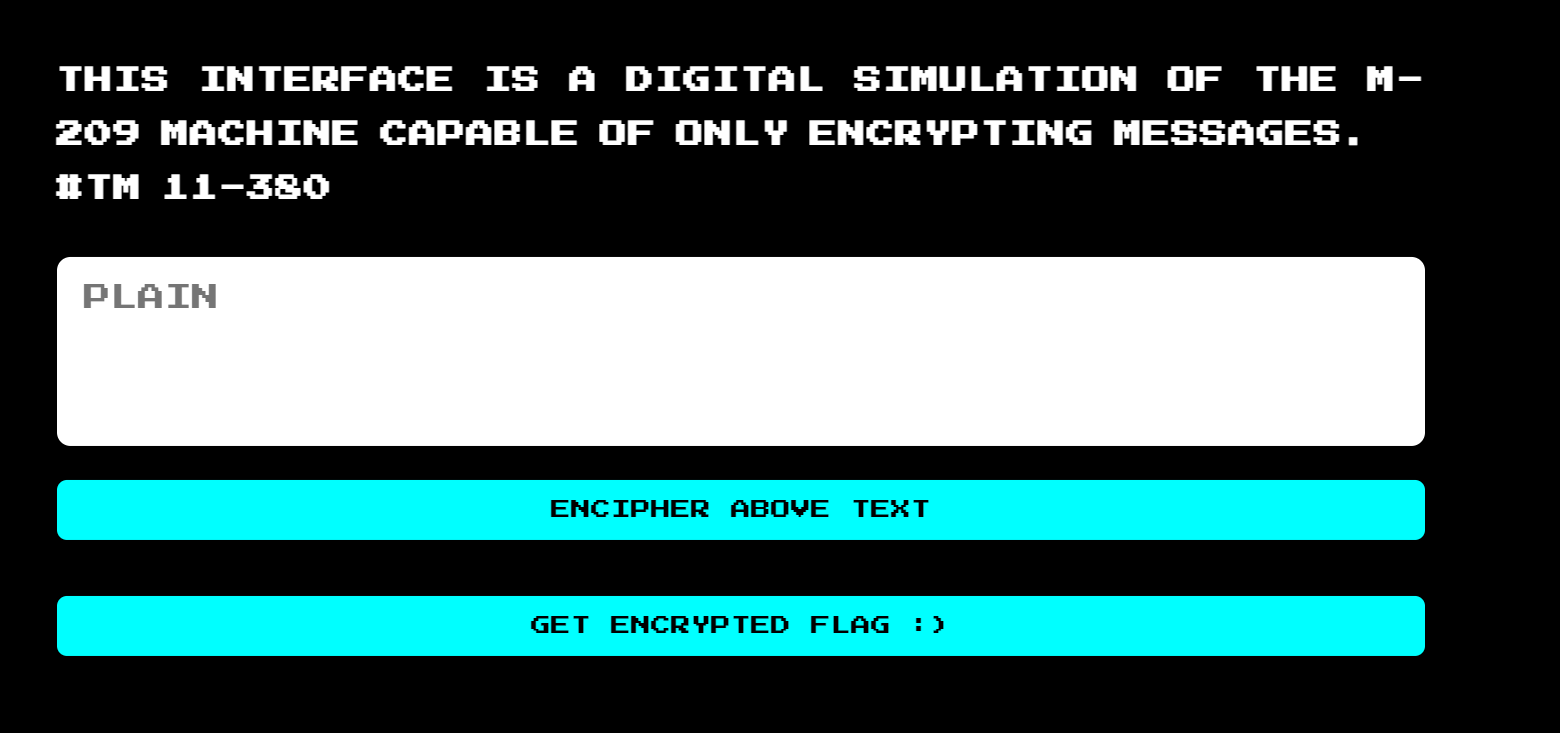
GET ENCRYPTDE FLAG :)
1 | {"flag": "ZZNVH EOOAA JSGPB DAKCP MQRGM MBXDT NAULS MYJRI USVAY WQGUK KEWRJ BAPPW YDWQU KFDHC OOOWF QVANE XLEEK MVFBX HYQOR SFKGU AKWEB LEPXV LHRCG MKMSO DVOZS JFESS LTUEY QUGAA IODSI IZEQJ ROTBS TKSEH JBORC ZZNVH EOOAA"} |
Thought
exp
1 | import requests |
result
medium
Aniely
分值:66
考点:爆破
challenge
There is stream cipher, try to keep it smooth!
1 | #!/usr/bin/env python3 |
Thought
exp
1 | #!/usr/bin/env python3 |
result
1 | b'CCTF{7rY_t0_D3cRyPT_z3_ChaCha20}' |
Diploma
分值:71
考点:
challenge
We are trying to solve matrix problem with only diploma! Here we go around the matrix!
1 | nc 08.cr.yp.toc.tf 37313 |
1 | [root@VM-0-7-centos ~]# nc 08.cr.yp.toc.tf 37313 |
Thought
1 | sage: M.multiplicative_order() |
exp
1 | import re |
result
1 | b'| Congrats, you got the flag: CCTF{ma7RicES_4R3_u5EfuL_1n_PUbl!c-k3y_CrYpt0gr4Phy!}\n' |
Oak land
分值:122
考点:离散对数
challenge
Where to publish the great work!
1 | #!/usr/bin/env python3 |
Thought
$c \equiv 110 \cdot e^x + 313 \cdot f^x+114\cdot g^x \pmod p$
$\to f \equiv e^y ,g \equiv e^z $
$\to c \equiv 110 \cdot e^{x} + 313 \cdot e^{xy} + 114 \cdot e^{xz} \pmod p$
$\to c \equiv 110 \cdot e^x + 313 \cdot e^{-x} + 114 \cdot e^{-2x} \pmod p$
exp
1 | c = 871346503375040565701864845493751233877009611275883500035764036792906970084258238763963152627486758242101207127598485219754255161617890137664012548226251138485059295263306930653899766537171223837761341914356 |
result
1 | b'CCTF{V33333rY_eeeeZy_DLP_cH41L3n9E!}' |
Cantilever
分值:79
考点:$p-1 \ is \ smooth$
challenge
What if you can find the message? If you can, that means you are genius, because we harden our crypto system with a very modern tool!
1 | #!/usr/bin/env python3 |
Thought
exp
1 | #!/usr/bin/env python3 |
result
1 | b'CCTF{5L3Ek_4s__s1lK__Ri9H7?!}' |
Side step
分值:146
考点:“侧信道”
challenge
I like to have my own pow!
1 | nc 01.cr.yp.toc.tf 17331 |
1 | #!/usr/bin/env python3 |
Thought
1 | if r == 4: t += 1 |
exp
1 | import re |
result
1 | b'| Great! you got the flag: CCTF{h0W_iZ_h4rD_D15crEt3_lO9ar!Thm_c0nJec7ur3?!}' |
Faonsa *
分值:180
考点:
challenge
Deploying the fault attack in real life is hard, we deployed it artificially!
1 | #!/usr/bin/env python3 |
Thought
exp
1 | from sympy import isprime |
result
1 | Congrats! your got the flag: CCTF{n3W_4t7aCk_8y_fAuL7_!nJ3cT10N_oN_p!!!} |
Resign
分值:122
考点:RSA,离散对数
challenge
Everything is up to you, I just want it to be verified!
1 | nc 03.cr.yp.toc.tf 11137 |
Thought
exp
1 | #!/usr/bin/env python3 |
result
1 | DEBUG] Received 0x124 bytes: |
DBB
分值:103
考点:椭圆曲线poh-hellman
challenge
Old school but fun hopscotch!
1 | #!/usr/bin/env sage |
Thought
$n= 11522256336953175349 \cdot 14624100800238964261 \cdot 203269901862625480538481088870282608241$
“子曲线:”
$m \cdot G \equiv Y \pmod n \to m \cdot G \equiv Y \pmod p \ if \ (p \mid n)$
PS:CRT的时候有坑
exp
1 | n = 34251514713797768233812437040287772542697202020425182292607025836827373815449 |
result
Fiercest
分值:142
考点:
challenge
Once again, we decided to deploy an artificial fault attack!
1 | nc 04.cr.yp.toc.tf 37713 |
Thought
diff(n,nextprime(n)) <= 2
$d \equiv e^{-1} \pmod {nextprime(n)-1}$
exp
1 | from sympy import * |
result
1 | [+] Opening connection to 04.cr.yp.toc.tf on port 37713: Done |
Mino *
分值:169
考点:-2进制?
challenge
You cannot have a good cryptosystem without mathematics! This task is an easy coding system!
1 | nc 02.cr.yp.toc.tf 13771 |
1 | #!/usr/bin/env python3 |
Thought
不太会哦,用z3大力好像可以,数学的分析好像也有,等我看看
exp
https://zhuanlan.zhihu.com/p/543272688
1 | import z3 |
result
1 | | Congrats, you got the flag: CCTF{MINO_iZ_4N_3a5Y_Crypto_C0d!n9_T4sK!} |
Starter ECC
分值:103
考点:模 n 开根
challenge
Dive deep to the elliptic cryptosystem!
1 | #!/usr/bin/env sage |
Thought
$y^2 \equiv x^3 + ax+b \pmod p$
这个 $n$ 不是素数,尝试分解
1 | sage: n=117224988229627436482659673624324558461989737163733991529810987781450160 |
exp
https://zhuanlan.zhihu.com/p/543272688
1 | q1 = 2^63 |
result
1 | b' CCTF{8E4uTy_0f_L1f7iN9_cOm3_Up!!} CCTF{8E4uTy_0f_L1f7iN9_cOm3_Up!!} CCTF{8E4uTy_0f_L1f7iN9_cOm3_Up!!} _______________________' |
medium-hard
Watery soup
分值:226
考点:构造
challenge
Watery soup
Find a message in a mess!
1 | nc 05.cr.yp.toc.tf 37377 |
1 | #!/usr/bin/env python3 |
Thought
$O(g) = (g^3 \cdot f) ^ {f-g} \cdot f + f^2 + g \pmod p$
如果直接解方程得话,因为 $f-g$ 不知道。所以想着能不能联立方程把这 $f$ 消掉。然后想着能不能找到两个 $g$,满足 $g_i^3 \equiv 1 \pmod p$ ,然后就有
$$
(O(g_1)-f^2-g_1)/(O(g_2)-f^2-g_2) \equiv (f^{f-g_1}f) / (f^{f-g_2}f) \equiv f^{g_2-g_1} \pmod p \
(O(g_1)-f^2-g_1) \equiv f^{g_2-g_1} \cdot (O(g_2)-f^2-g_2) \pmod p \
(O(g_1)-f^2-g_1) - f^{g_2-g_1} \cdot (O(g_2)-f^2-g_2) \equiv 0 \pmod p
$$
但是这个degree $(g_2-g_1)$ 太大了,如果控制 $g_2-g_1$ 的值
$$
(O(g_1)-f^2-g_1)/(O(g_2)-f^2-g_2) \equiv (g_1^{3f-3g_1}f^{f-g_1}f) / (g_2^{3f-3g_2}f^{f-g_2}f) \equiv (\frac{g_2^{3f-3g_2}}{g_1^{3f-3g_1}})f^{g_2-g_1} \pmod p \
$$
右式前面那一大块还是有 $f$,
除法不行再来看看乘法,因为有负幂次
如果 $(O(g_1)-f^2-g_1) \cdot (O(g_2) -f^2-g_2) \equiv (g_1^3 \cdot f)^{f-g_1} \cdot f \cdot (g_2^3 \cdot f)^{f-g_2} \cdot f \equiv (g_1g_2)^{3f}/g_1^{3g_1}g_2^{3g_2} \cdot f^{f+1} \cdot f^{f+1} / f^{g_1+g_2} $
这里能不能控制 $g_1g_2=\pm 1,g_1+g_2 = 0$,但是要求 $64\lt g.nbits() \lt 128$,而且还有一个 $f^{2f+2}$ 呢。
如果要处理掉那个 $f^{2f+2}$ ,我们可以给两个交互的值做一个幂次,即原式改为
$$
(O(g_1)-f^2-g_1)^X \cdot (O(g_2) -f^2-g_2)^Y \equiv (g_1^Xg_2^Y)^{3f}/g_1^{3g_1X}g_2^{3g_2Y} \cdot f^{X(f+1)+Y(f+1)} / f^{g_1X+g_2Y}
$$
那就考虑 $g_1^Xg_2^Y=1,g_1X+g_2Y=0,X+Y=0$
显然这里要求$X=-Y$,那就需要 $g_1=g_2=1$ 了,不太行
那我们就再加一条变量
$$
g_1^Xg_2^Yg_3^Z=1,g_1X+g_2Y+g_3Z=0,X+Y+Z=0
$$
姑且设 $X=Y=1,Z=-2$
就有 $g_1g_2 \equiv g_3^2,g_1+g_2\equiv2g_3$
似乎只有 $g_1=g_2=g_3$ 才能满足这些条件,但这显然不符合题目要求。
我们再设 $X=1,Y=2,Z=-3$
就有 $g_1g_2^2\equiv g_3^3,g_1+2g_2\equiv 3g_3$
我们有 $g_1 =-8g_2 ,g_3 = -2g_2$
然后我们就有
$$
(O(g_1)-f^2-g_1)^1 \cdot (O(g_2) -f^2-g_2)^2\cdot(O(g_3) -f^2-g_3)^{-3} \equiv (g_1^Xg_2^Yg_3^Z)^{3f}/g_1^{3Xg_1}g_2^{3Yg_2}g_3^{-3Zg_3} \cdot f^{(f+1)(1+2-3)} / f^{g_1X+g_2Y+g3Z} \ \equiv 1/g_1^{3g_1}g_2^{6g_2}g_3^{-9g_3} / f^{g_1X+g_2Y+g3Z}
$$
注意到这里是 $g_1X+g_2Y+g_3Z \equiv 0 \pmod p$,实际上 $3p-8g_2 + 2g_2+ -6g_2+-3p = 0$ 所以上式右手边为
$$
1/g_1^{3g_1}g_2^{6g_2}g_3^{-9g_3}
$$
所以
$$
(O(g_1)-f^2-g_1)^1 \cdot (O(g_2) -f^2-g_2)^2 \cdot g_1^{3g_1}g_2^{6g_2}g_3^{-9g_3} =(O(g_3) -f^2-g_3)^{3}
$$
PS:这里用的前面的脚本找的 $p-1$ 光滑的 $p$,也不知道有没有必要就是说(因为前面有求离散对数的想法…..)
exp
1 | #!/usr/bin/env python3 |
result
1 | b'CCTF{Pl34se_S!r_i_w4N7_5omE_M0R3_5OuP!!}' |
313 Loyal
分值:209
考点:paillier cryptosystem, Homomorphic properties
challenge
I have developed a probabilistic asymmetric algorithm for public key cryptography. Then I added some functions to harden it, you can try this oracle now. But I think it is still unbreakable! What about you?
Note: The source code updated, please download again!
1 | nc 07.cr.yp.toc.tf 31377 |
Thought
同态走一波,交互中的处理解密后相当于
$m_i = r\cdot (D(poly[0]) \cdot f_i + D(poly[1]) \cdot f_i^2 + D(poly[2]) \cdot f_i^3 \cdots) + f_i$
poly给个 $[E(0),E(0)]$,然后解密就能直接得到明文 y4HCcRRMt{h!PF_00nOT71e3o3N0RCn_C5}pmH_C3!M
被最后 shuffle(result) 了,所以我们得构造一下,留一个标志
23333,不用了就是说,题目有POINTS.sort(),
exp
1 |
|
result
1 | CCTF{4n0t3R_h0MomORpH1C_3NcRyP7!0n_5CH3Me!} |
Soda*
分值:209
考点:signature forge
challenge
You may ask yourself how factoreal is skipping RSA? Here he comes with this one!
1 | nc 01.cr.yp.toc.tf 37711 |
1 | #!/usr/bin/env python3 |
Thought
$e = 2 \cdot (g^{m^2}%n) % 2^{152}) \oplus 1$
这里用的是 $m^2$
限制不让 $s=m$
emmmm,但是没说不让 $s=-m$
exp
result
1 | [root@VM-0-7-centos ~]# nc 01.cr.yp.toc.tf 37711 |
Sparse*
分值:114
考点:RSA
challenge
RSA is fun, the frozen RSA is even more fun!
1 | #!/usr/bin/env python3 |
Thought
$p,q$ 有小于十个不同的比特。
(由于题目的p,q仅有一个比特不同,所以很容易遍历,但是如果有10个比特不同,很难想象,应该有别的方法)
exp
1 | from Crypto.Util.number import * |
result
1 | b'CCTF{5pArs3_dIfFeRenc3_f4ct0r1za7iOn_m3th0d!}' |
Larisa
分值:174
考点:SymmetricGroup
challenge
You think you can understand the way our cryptosystem encrypts messages? Here you can challenge yourself by decrypting this message!
1 | #!/usr/bin/env sage |
Thought
组了一个多维的SymmetricGroup,然后实现了一下幂运算。用的最经典的那个平方乘方法
并不能把他看作是一个矩阵,,因为做幂次运算的时候,每一行都仅与自己相关,所以在做幂次运算的时候,其实也可以给他拆开来一行一行做
1 | def prodlat(A, B): |
加密是$C = M^e$,我们可以拿到阶,计算一下逆元,再乘回来就好了
exp
https://remyoudompheng.github.io/ctf/cryptoctf2022/larisa.html
1 | t = [[...]] |
result
1 | b'the flag: CCTF{pUbliC_k3y_crypt0graphY_u5in9_rOw-l4t!N_5quAr3S!}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}' |
Shaim
分值:226
考点:分组哈希
challenge
1 | Do you believe that every hash function has weaknesses? If yes, can you find any collision? |
Thought
$h1 = msg+length+padding$
$h2 = Sbox(h1)$
$H_0 = h2[0]$
$H_i = E(H_{i-1}) \oplus H_{i-1} \oplus h2_i$
$hash = sha256(H_{-1})$
想要哈希一样的话,我们其实只用管最后一组就好,不过最后一组是length+padding或者纯padding,我们不能随意控制。
换个想法,由于后一组的结果与前一组相关,我们也可以控制前面的值,让其到达后面的值与原值一致即可。
考虑前三组,
$H_0 = h2_0$
$H_1 = E(H_{0}) \oplus H_{0} \oplus h2_1$
$H_2 = E(H_{1}) \oplus H_{1} \oplus h2_2$
我们只要更改 $h2_0,h2_1$ 为 $$h2_0’,h2_1’$$,使得后面的 $H_1’ = H_1$ ,这样后面也就都有 $H_i’ = H_i$ 即可满足条件。
若改为 $h2_0’$,那么 $H_1’ = E(H_0’) \oplus H_0’ \oplus h2_1$
想要让 $H_1’ = H_1$
可以两边同时异或 $H_1’ \oplus H_1$
则有 $H_1 = E(H_0’) \oplus H_0’ \oplus h2_1 \oplus H_1’ \oplus H_1$
于是我们设 $h2_1’ = h2_1 \oplus H_1’ \oplus H_1$
不过就是说,想要走到 $h2$,还得过一个 $Sbox$,所以我们控制 $h2$ 的话,得先逆一个 $Sbox$ 去控制 $msg$,然后题目很恶心的用了 $utf-8$,就没那么随心所欲了。需要en爆。这里我们每次随机控制 $msg_1$,然后计算 $msg_2$,遇到符合要求的,就传过去。
exp
1 | from Crypto.Util.number import * |
result
1 | [root@VM-0-7-centos ~]# nc 01.cr.yp.toc.tf 37113 |
Lagima
分值:164
考点:SymmetricGroup
challenge
You are in the road to learn some interesting cryptosystems, decrypt our cipher!
1 | #!/usr/bin/env sage |
前面那个求底数,现在这个求指数了。
Thought
对称群的一个数学性质,之前也不知道,看题解发现的
exp
https://remyoudompheng.github.io/ctf/cryptoctf2022/lagima.html
1 | import json |
result
1 | b'3lGam4L_eNcR!p710n_4nD_L4T!n_5QuarS3!' |
Versace
分值:226
考点:大整数分解
challenge
What is most important when we have prime numbers? Answer and decrypt the message!
Note: The output file has changed, Please download again!
1 | #!/usr/bin/env python3 |
Thought
想要解密肯定是要先算出 $fi^u \cdot th^v \cdot (k+1)^e$
题目给出了 $n,e,fi,th,k^e,5^u,13^v$
那么我们需要解出 $k,u,v$
其中 $k$ 要大整数分解
$u,v$ 要解离散对数
只要能够分解这个 $n$ 就好了。
发现使用 Williams p+1 可以给这 $n$ 秒分了,
然后 $p-1 = 2^{18} \cdot 3^{30} \cdot 7^{53} \cdot 11^{12}$,好解离散对数
但是另一半似乎有点难搞,
chao,多运行几次,会发现结果不一样,原来有三个因子,都是这样子的形式。
分解之后分别在 $p,q,r$ 求离散对数,求 $m$,最后给 $m$ 走一个 crt 就好了。
exp
1 | from gmpy2 import iroot,gcd |
result
1 | b'CCTF{8As3d_oN_f4c70r1n9_4nD_d15cr3tE_lOgaRiThM!}' |
hard
GSDP
分值:164
考点:
challenge
A very modern cryptography! Break it harder!
1 | #!/usr/bin/env sage |
Thought
u,v那么小,,爆
exp
1 | n=20474248118672564431085568112167867588651829 |
result
1 | PKCS_N0n_cOmMu74T!v3_rIn9 |
Persian cat
分值:247
考点:block cipher
challenge
Persian cat
Can you check this crypto system and let us know the message? You will find this crypto system very adroit!
1 | nc 03.cr.yp.toc.tf 11173 |
1 | #!/usr/bin/env python3 |
Thought
代码过于长了,加密的内容也好麻烦好绕,看着让人头大。不过细看一下,似乎也就是一个纸老虎
注意到 encrypt 函数,
1 | def encrypt(msg, key): |
是块加密,一次加密32个比特,加密公式为
$c_0 = Enc(m_0,k)$
$c_i = Enc(m_i,g(m_{i-1}) \oplus c_{i-1})$
有那么有点 $CBC$ 模式的味道。
注意到我们在交互的时候,传入 $msg$,会返回 $c = encrypt(msg+flag,k)$
那么进行一手逐字节爆破就可以了吧。第一次传入 “A” * 31,那么第一组就会是 “A”*31 + flag[0] 的密文,我们爆破这个字节就好了。以此类推可以获取flag的前32个字节。那后面的字节怎么办呢?
那我们可以第一次传入 “A” * 64,看第二组的密文来开始爆,这样能爆出 $flag$ 的64个字节,以此类推。。。(怪不得给了这么多地址)
但是春哥顶啊,直接就是对波斯猫的一个硬撸。
exp
NLCS x
分值:375
考点:LFSR、PolynomialRing
challenge
1 | #!/usr/bin/env sage |
是没有解出来的题目,那么,就留给大佬了~
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可联系QQ 643713081,也可以邮件至 643713081@qq.com
文章标题:2022 CryptoCTF
文章字数:16.8k
本文作者:Van1sh
发布时间:2022-09-14, 17:16:00
最后更新:2023-03-07, 18:35:03
原始链接:http://jayxv.github.io/2022/09/14/2022 cryptoctf/版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。

